IN THE SPOTLIGHT: MDE to MDB Conversion Service
(also supports: ACCDE to ACCDB, ADE to ADP, etc)
IN THE SPOTLIGHT: Access Database Repair Service
An in-depth repair service for corrupt Microsoft Access files
IN THE SPOTLIGHT: vbWatchdog
VBA error handling just got easier...

" vbWatchdog is off the chart. It solves a long standing problem of how to consolidate error handling into one global location and avoid repetitious code within applications. "
- Joe Anderson,
Microsoft Access MVP
Meet Shady, the vbWatchdog mascot watching over your VBA code →
(courtesy of Crystal Long, Microsoft Access MVP)
IN THE SPOTLIGHT: vbMAPI
An Outlook / MAPI code library for VBA, .NET and C# projects
Get emails out to your customers reliably, and without hassle, every single time.
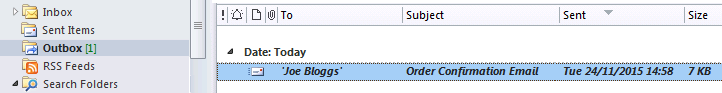
Use vbMAPI alongside Microsoft Outlook to add professional emailing capabilities to your projects.
IN THE SPOTLIGHT: Code Protector
Standard compilation to MDE/ACCDE format is flawed and reversible.
We often get asked what measures do we employ to protect against the illegal reverse engineering of a project without consent from the owner. Therefore we have decided to release the following details which explain the standard checks we make to try to protect against this scenario.
We obtain the compiled database in question along with details of the customer initiating the conversion.
We evaluate the compiled file to ensure suitability and to gather developer contact information from multiple sources, including (but not exclusively);
Forms/Reports (e.g. splash screens, about screens, logos etc)
Summary Information within Access
VBA code (e.g. VBA strings containing 'Please contact support on xxx' or '(c) EverythingAccess.com 2005')
Please note: this is not an extensive list as we don't particularly wish to expose all the methods we use to identify the owner for obvious reasons.
If the developer information is not disclosed, is unclear or is ambiguous in any way then we simply refuse the conversion on these grounds.
We research the contact information obtained in (2) and the specific application details (application name etc) - the aim being to verify the accuracy of the information and to try to spot any obvious signs of illegal activity. This research is conducted on the internet and by any other means as appropriate.
We verify the customer initiating the conversion is an employee of the "owner" (or the customer is the owner) as described in (2). Contacting the company/developer involved by telephone using the information obtained in (2) is a common check here. Also, e-mail addresses are checked for the correct domain names associated with the company/developer involved.
We request a signed statement from a director of the company or individual developer (using info obtained in (2)) that clearly the states the reason for the requested MDE conversion, an affirmation certifying legal ownership and granting us permission to reverse engineer the compiled file on your behalf.
If any of the above checks fail or appear to be misleading or ambiguous, then we simply refuse to do the conversion.
Remember, we are professional developers ourselves and understand the concerns that other developers may have about the service we offer. If we have even the slightest concern of the legality of the requested conversion then we will not proceed under any circumstances.
TWINBASIC LTD (Company No. 16590181, VAT No. GB497509439)
Terms | Privacy | Sitemap | X (Twitter)